Thank to Chris Laprise I have now a great update script for my Qubes installation.
I know it’s bad habit to pollute dom0, but I looked distrustfully 😉 through the code and it seems efficient and not in any way harmful.
First we get with git 😉
If you are like me, you don’t want your template to have git, but only install it every time you need it ;), do the following and fedora-26 is polite and helps you out:
In appVM/dispVM, etc.
git clone https://github.com/tasket/Qubes-scripts.git
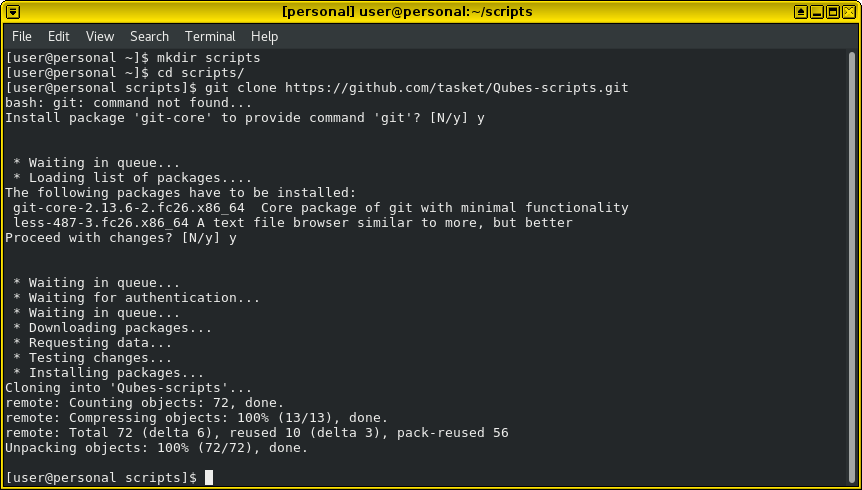
For now we only need the 1 script:
In dom0:
qvm-run --pass-io <src-vm> 'cat /path/to/file_in_src_domain' > /path/to/file_name_in_dom0
Now we have it in dom0:
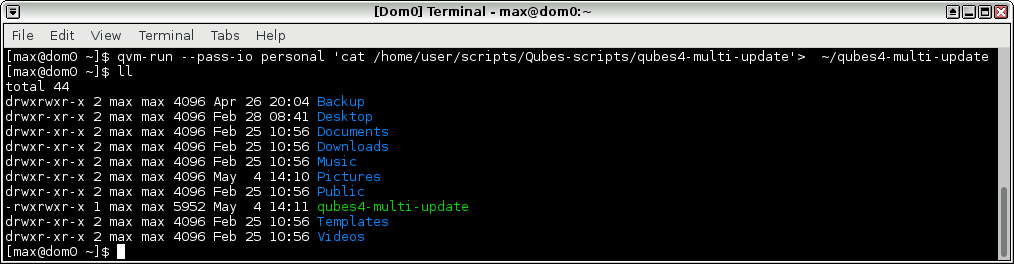
We can try it out on a fedora-26 template:
in dom0:
./qubes4-multi-update -l fedora-26
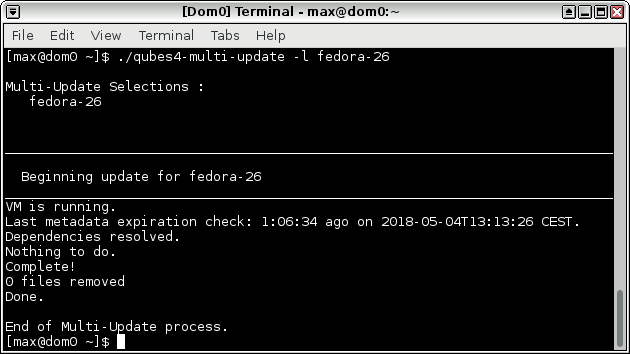
Boom, already updated, but you get the picture.
The following command updates only templates with available updates. That should suffice for generic usage.
./qubes-multi-update -a -l -t
I found a small error when running an update on whonix-ws, but otherwise it runs beautifully.
UPDATE 2018-05-04:
When using Qubes 3.2 running the above command includes the standalone VM’s. Just so you know.
UPDATE 2018-12-28:
Chris has updated the script (ref: https://groups.google.com/d/msg/qubes-users/YKAp0_1MFfk/mTyQTM9JEgAJ)
Now I use with unattended and everything just rolls through, nicely:
./qubes-multi-update -a -l -t-u


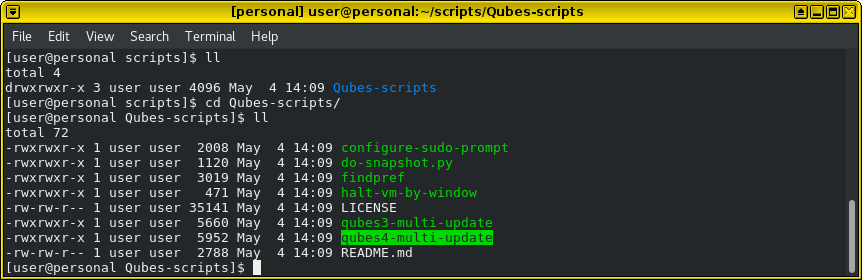
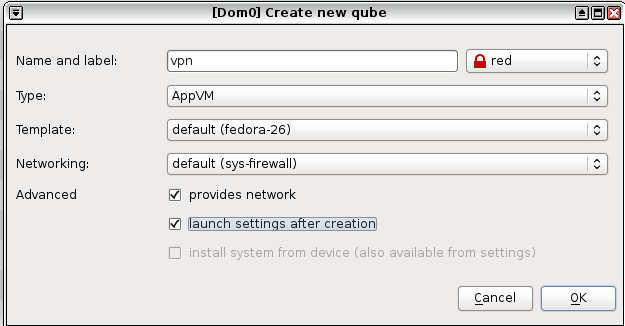
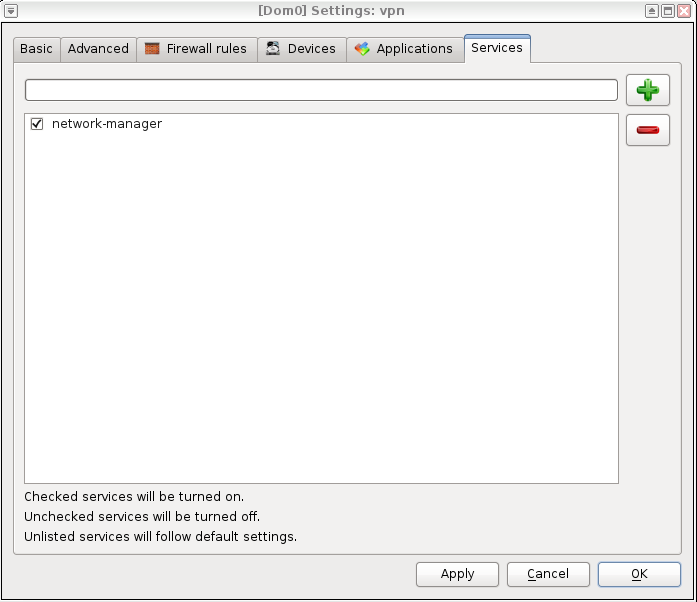
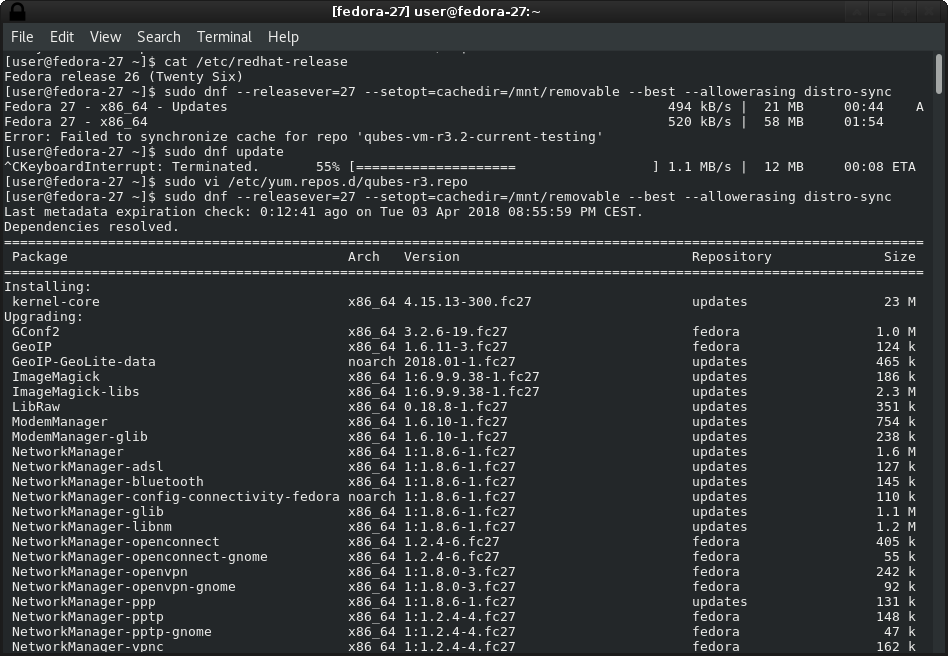
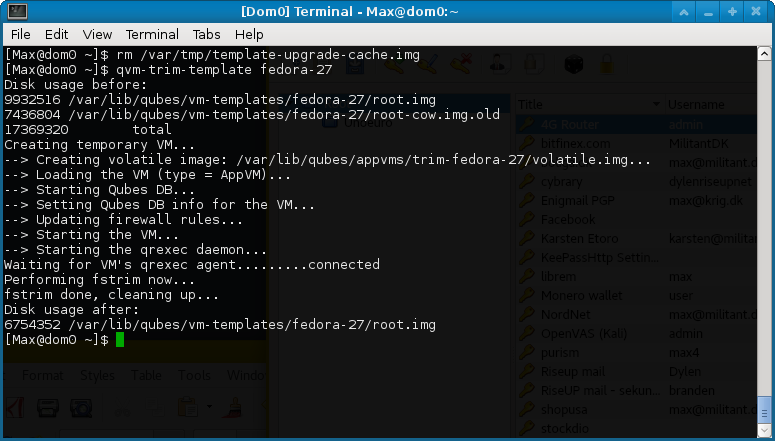
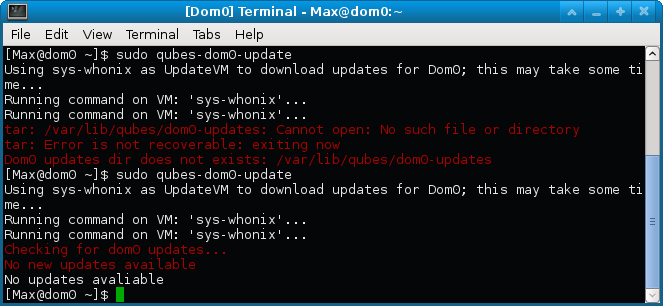
 Choose scan to see if everything is in order:
Choose scan to see if everything is in order: